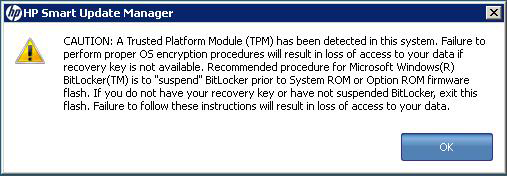
The TPM, when used with BitLocker, measures a system state and, upon detection of a changed ROM image, restricts access to the Windows file system if the user cannot provide the recovery key. HP SUM detects if a TPM is enabled in your system. If a TPM is detected in your system or with any remote server selected as a target, for some newer models of ProLiant servers, HP SUM utilities for HP iLO, Smart Array, NIC, and BIOS warn users prior to a flash. If the user does not temporarily disable BitLocker and does not cancel the flash, the BitLocker recovery key is needed to access the user data upon reboot.
A recovery event is triggered if:
You do not temporarily disable BitLocker before flashing the system BIOS when using the Microsoft BitLocker Drive Encryption.
You have optionally selected to measure HP iLO, Smart Array, and NIC firmware.
If HP SUM detects a TPM, a warning message appears.
To enable firmware updates without the need to type in the TPM password on each server, the BitLocker Drive Encryption must be temporarily disabled. Disabling the BitLocker Drive Encryption keeps the hard drive data encrypted. However, BitLocker uses a plain text decryption key that is stored on the hard drive to read the information. After the firmware updates have been completed, the BitLocker Drive Encryption can be re-enabled. Once the BitLocker Drive Encryption has been re-enabled, the plain text key is removed and BitLocker secures the drive again.
NOTE: Temporarily disabling BitLocker Drive Encryption
can compromise drive security and should only be attempted in a secure
environment. If you are unable to provide a secure environment, HP
recommends providing the boot password and leaving BitLocker Drive
Encryption enabled throughout the firmware update process. This requires
setting the | |
To temporarily disable BitLocker support to allow firmware updates:
Click Start, and then search for
gpedit.mscin the Search Text box.When the Local Group Policy Editor starts, click Local Computer Policy.
Click Computer Configuration → Administrative Templates → Windows Components → Bitlocker Drive Encryption.
When the BitLocker settings are displayed, double-click Control Panel Setup: Enable Advanced startup options.
When the dialog box appears, click Disable.
Close all windows, and then start the firmware update.
To enable advanced startup options:
Enter
cscript manage-bde.wsf -protectors -disable c:When the firmware update process is completed, the BitLocker Drive Encryption support can be re-enabled by following steps 1 through 4 but clicking Enabled in step 5 instead. The following command can be used to re-enable BitLocker Drive Encryption after firmware deployment has completed.
Enter
cscript manage-bde.wsf -protectors -enable c:
The following table describes TPM detection scenarios that you might encounter.
| Scenario | Result |
|---|---|
| If TPM is detected and enabled, the installation is not silent, and a system ROM must be updated. | A warning message appears. Select OK to continue. The installation is not canceled. |
If TPM is detected and enabled, the installation is silent,
the /tpmbypass switch is not
given, and any firmware updated must be applied to the server. |
No warning appears. A new log file is generated (%systemdrive%\cpqsystem\log\cpqstub.log).
Because the installation is silent, the installation is terminated
and cannot continue. |
| If TPM is detected and enabled with Option ROM Measuring, the installation is not silent, and a system ROM must be updated. | A warning message appears. After selecting OK, you can continue. The installation is not canceled. |
If TPM is detected and enabled with Option ROM Measuring,
the installation is silent; the /tpmbypass switch
the installation is silent, the installation is terminated and cannot
continue. is not given, and any firmware updated must be applied to
the server. |
No warning appears. A new log file is generated
(%systemdrive%\cpqsystem\log\cpqstub.log).
Because the installation is silent, the installation is terminated
and cannot continue. |
If TPM is detected and enabled, the installation is silent,
The installation occurs. and the /tpmbypass switch
is supplied. |
The installation occurs. |